Adverse Selection and Moral Hazard in Anonymous Markets
Contributed by Nicolas Grekas in 26921. This is possible because of donations from our community. This action follows the arrest on Nov. The official Security Onion 2 AMI. Substantial assistance was provided by the U. To use this feature you will need an individual account. “According to the indictment unsealed today, these defendants allegedly made millions of dollars by providing a gateway to illegal Darknet marketplaces, allowing hundreds of thousands of users to buy fentanyl, hacking tools, stolen credit cards, and other contraband,” said Assistant Attorney General Benczkowski. Before the introduction takes place, the client in this case, you picks a Tor relay and establishes a circuit Onion nemesis market to it. You will be notified whenever a record that you have chosen has been cited. Add a description, image, and links to the darknet markets topic page so that developers can more easily learn about it. Furthermore, online activity increased during the pandemic, thereby serving favorable conditions for boosting the momentum of the crypto market and attracting new investors. We found several thousand vendors selling tens of thousands of stolen data products on 30 darknet markets. Its user friendly interface enhances its accessibility, making it an attractive platform for both new and experienced users. If you wanna lose your money, give it to Nemesis. While it included some innocuous listings such as health supplements, the majority of vendors and most of the sales were related to illicit drugs. Nobody can trace your purchases at Nemesis, so you can buy all the ridiculous things drugs you want without anyone judging you. Tor2web functions in this way, but you shouldn’t use it. 00 larger spacing available, please enquire. Wani MH, Bazaz NH, Paul RK, Itoo SA, Bhat A. Alright, so first of all you wanna make sure that you have a web server up and running. In this explainer piece, we’ll cover what a darknet marketplace “DNM” is, how administrators obfuscate their infrastructure, and why in the case of Hydra and several other recent takedowns, law enforcement and regulators were able to identify and disrupt the marketplaces. To confirm the location of our Tor installation and configuration, we can use whereis. Or on the bench seating by the kitchen. You can find others listed on our crypto exchanges page. Because some markets do not classify product listings or misclassify listings, we used a set of keywords to extract the relevant listings for the analysis see Appendix I for a full list of keywords. Remember to encrypt the message using their PGP key if you’re going to be sending any sensitive information such as an address.
Bibliographic and Citation Tools
Dark pools are private exchanges for trading securities that are not accessible by the investing public. Subscribe now and grab a 15% discount voucher. Hydra could eventually come to the English speaking world as well. “Our Cyber Crimes Unit once again used their cryptocurrency tracking expertise to help take down this site and identify the criminal behind it. On the dark web, anything goes, whether it be illegal drug sales, hacker forums, or things much, much darker. Upon starting Tor for the first time with our new configuration, an. Ten days after UniCC announced its retirement but slightly before the announced closure date, it was reported that Russia’s Federal Security Service FSB had detained the site’s alleged operator: Andrey Sergeevich Novak. You will be notified whenever a record that you have chosen has been cited. To understand what DNMs are and how they operate, it’s important to first clarify that there are actually three different layers of the Internet. The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is an award winning media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. A verified list of darknet markets and services with links for educational reference. Before that moment, I had never heard of the darknet. ProtonMail is a Swiss based encrypted email service that doesn’t require personal information when you sign up. So, data, a tool, or a service can occur in these black markets. Here, we examine a large sample of offenders and explore the properties that lead them to move to specific online spaces.
About ANONYMOUS
The current study empirically tests these hypotheses by reconstructing vendor flows across digital marketplaces before and after a major law enforcement interdiction. To this end, we reviewed a sample of studies for critical aspects concerning research in the context of Tor. The external trade by country in NEMESIS takes two directions: intra EU trade and trade with the rest of the world. We will continue to investigate, expose, and take action against criminal networks no matter where they operate. The dark web and deep web are not the same — all sites on the dark web are technically part of the deep web, but much of the deep web is not part of the dark web. STATUS: Up and Working Fine. Alternatively, you can take a snapshot of a web page that you consider important and want to ensure is archived for freedom of information purposes. After that I placed two orders with Thebreakingbad. For this, a Tor node must be assigned the HSDir flag. Onion sites when known. Check out our rundown of the best dark web links and how to navigate dark websites safely. Tesla and Microstrategy lose $1. Many stock exchanges, such as the London Stock Exchange LSE, Toronto Stock Exchange TSX, New York Stock Exchange NYSE, and NASDAQ, as well as dark pools, offer anonymous trading for certain users. 2 billion transactions between February 2011 and July 2013. Hypothesis 2: A law enforcement disruption will strengthen the relationship between current vendor flows and where vendors peers’ have moved to in the past. BTW: Arch Linux is listed at. Using a Nemesis Market with a lot of vendors was so convenient that I’m pretty sure I bought something from every single one of them. You can view pending or past orders at any time in the ‘Orders’ section found in the top left corner on every page. AlphaBay was relaunched by DeSnake in August 2021 with a new design but with the same admin as before and is once again planning to become the biggest darknet market in history. KillNet’s Telegram forum is a different form created by managing multiple chat groups from the same hand; this forum also includes a market that offers the same services. Beware, though: Sci Hub can come with Always check local laws before accessing any paid for material. The market now has an established reputation among cybercriminals, which means that any stolen credentials for sale on there are likely to provide valid access to systems, services, or apps. Configuring a local web server for your hidden service is exactly the same as with Onion v2, just make sure that your web server is accessible locally on 127. Although the best engineers are currently tweaking and updating the algorithm, no human has verified the price predicted below, so please use your discretion and make a decision wisely. It’s time for our annual peek behind the curtain into the recesses of the dark web.
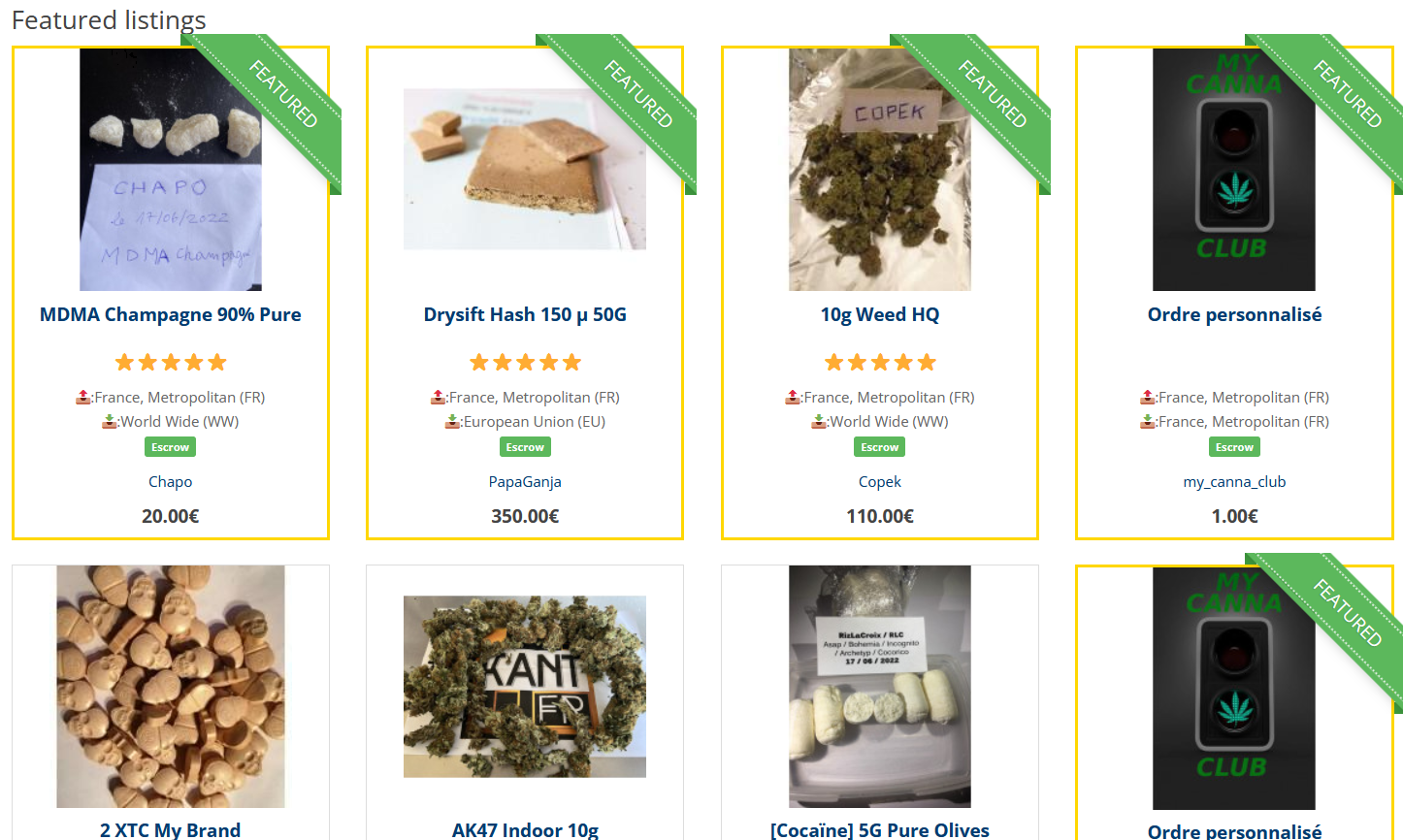
What are the most popular things for sale on the darknet?
This dark web search engine also has an easy to use interface and offers free access to onion links and websites. First, we need to be in the directory that contains the content we would like to host. We access restricted channels and automate intelligence gathering to anticipate attacks targeting your organization, employees, and customers. This dataset has the advantage of displaying anonymous trades on all stocks listed on TSX. Delft University of Technology. WayAWay, an old dark web forum, has been re observed on the dark web. 31% are assigned to seven similarity groups and 20% of all analyzed vendor sites are duplicates. Maximum likelihood estimation and inference on cointegration with application to demand for money. When accessing an authenticated onion service, Tor Browser will show in the URL bar an icon of a little gray key, accompanied by a tooltip. A host is basically a website’s house, or where it lives and takes up space. Unravel the enigma and gain a deeper understanding of this hidden realm on the internet. 2 billion in cryptocurrency. After a meteoric rise in the past decade, many industry experts have questioned whether it could lead to the next crypto bull market. Several makers recalled how Faire initially sold their products without notifying them or requesting permission, and there was plenty of moaning about a lack of transparency or a dearth of information about how Faire works. Get your free trial here. Dark web websites are not listed on regular search engines, but dark web search engines can help you find them. It is necesary to have discovery and analysis approaches to collect and analyze Tor hidden services. Hacking vendors commonly offered to illegally access online accounts of the buyer’s choosing. But remember — no program can protect your device against everything. Big companies are working on projects for tokenizing individual subsidiaries. Phan and Prihar communicated on a daily basis to facilitate their criminal enterprise. You can check these out if you like, or search from our vast array of categories, or conduct a search using the search bar at the top of the page. We thank German authorities and the Bundeskriminalamt, the German Federal Criminal Police Office, for its valued assistance in this case. Uncomment these lines to open port 8000 for Nginx and while you are at it, don’t forget to comment out port 8080 lines cause you don’t want Nginx listening on two ports, that just doesn’t work. Katie Petrillo, senior manager of LastPass product marketing at LogMeIn, said her company’s dark web monitoring service introduced last August is provided as part of its overall password management offering for paying LastPass customers, including LastPass Enterprise end users. The Justice Department announced today a disruption campaign against the Blackcat ransomware group — also known as ALPHV or Noberus — that has targeted the computer networks of more than. Onion where XYZ is a sixteen digit name that is unique and is generated using the public key of the service. In The 17th International Conference on Availability, Reliability and Security ARES 2022, August 23–26, 2022, Vienna, Austria. The US’ particular brand of economic resiliency this year has been driven by high levels of government spending as well as near shoring efforts to strengthen the domestic manufacturing sector, among other things. Encrypt your internet connection automatically with Avast SecureLine VPN.
Infinity: A Black Market under a Hacker Forum
Two megacap assets – bitcoin and ether – dominate 70% of the market capitalization for digital assets. Investigating causal relations by econometric models and cross spectral methods. “Underground websites such as Silk Road and Silk Road 2 are like the Wild West of the Internet, where criminals can anonymously buy and sell all things illegal,” said HSI Associate Director Edge. IOS: Cake Wallet from clearnet link. Threat Command can help identify threat actors and their intentions with broad coverage of dark web sources. Debian also provides torified download mirrors, via apt transport tor and tor+ight now none of these Arch pages even mention Tor. The important point to note is that Hidden Services are not protocol aware they just redirect raw packets. Also, the market does provide a mnemonic code just after registration. It’s an interesting time pass — until you discover something controversial on past versions of government or corporate websites.
2 Ahmia
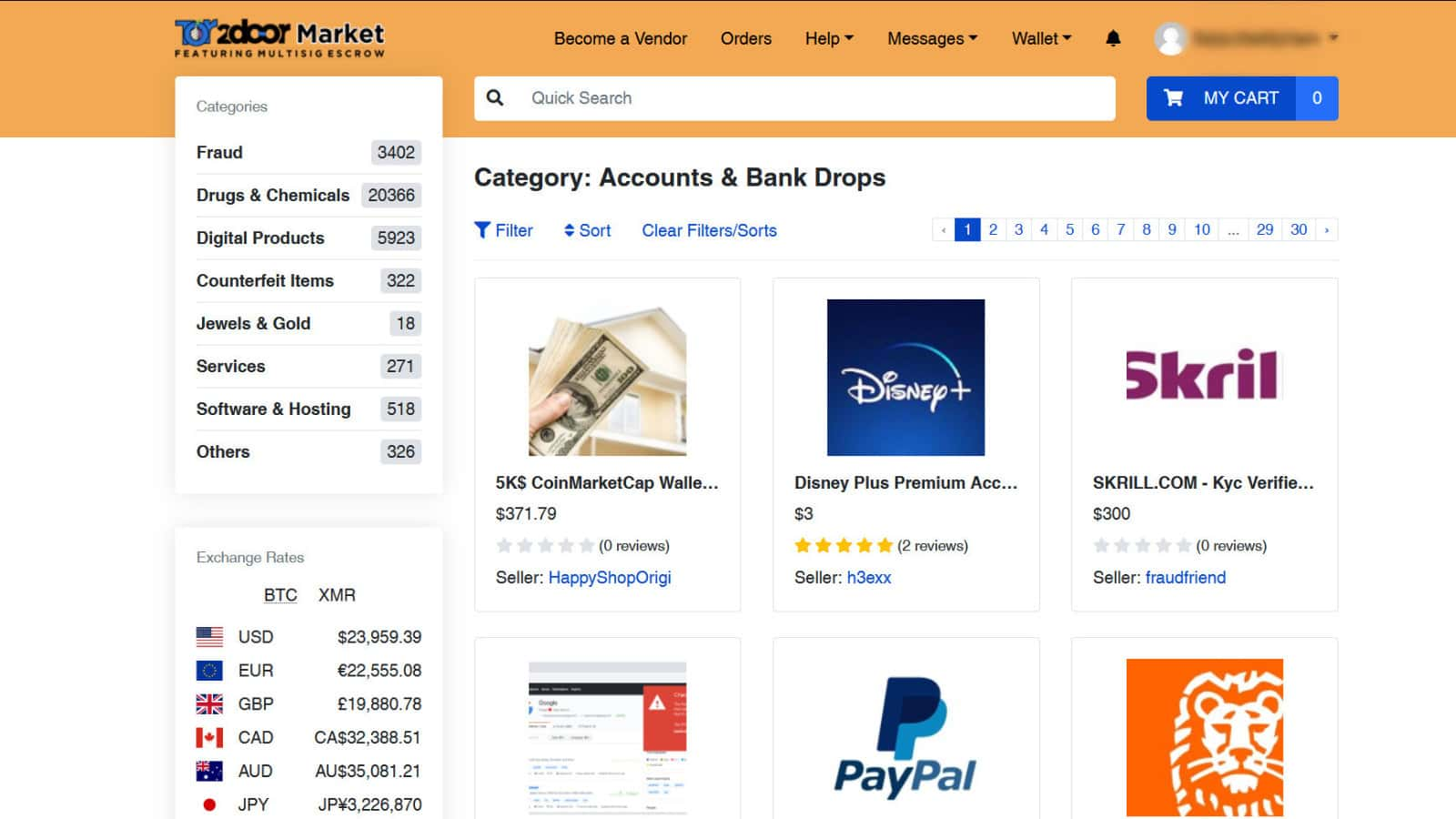
To see all brands in all categories, download the full data sheet. Dark web websites offer privacy, anonymity, content, and goods that you can’t get on the surface web. Second, this connectivity persists before and after a major law enforcement intervention. So, what’s driving that downturn. Nemesis Market supports direct pay at the checkout yep, just like Amazon, although you can still deposit to a wallet first if you choose. Several of the most prominent fraud shops – including Bypass Shop and Brian Dumps – appeared to face issues or shut down in 2022, according to Chainalysis, but it is still unclear why. Corporate heavyweights, led by the financial sector, are paying vendors big bucks to illuminate what’s happening on hidden sections of the internet. KWADRON Cartridge System 0. Nemesis market is awesome. Indeed, while similar to other developed countries, Canada’s economy is increasingly dominated by the service sector, but the energy industry is still a major contributor Policy Brief, 2016. No need for any fiddly alignment. I did not expect that.

Bugs2023 11 04
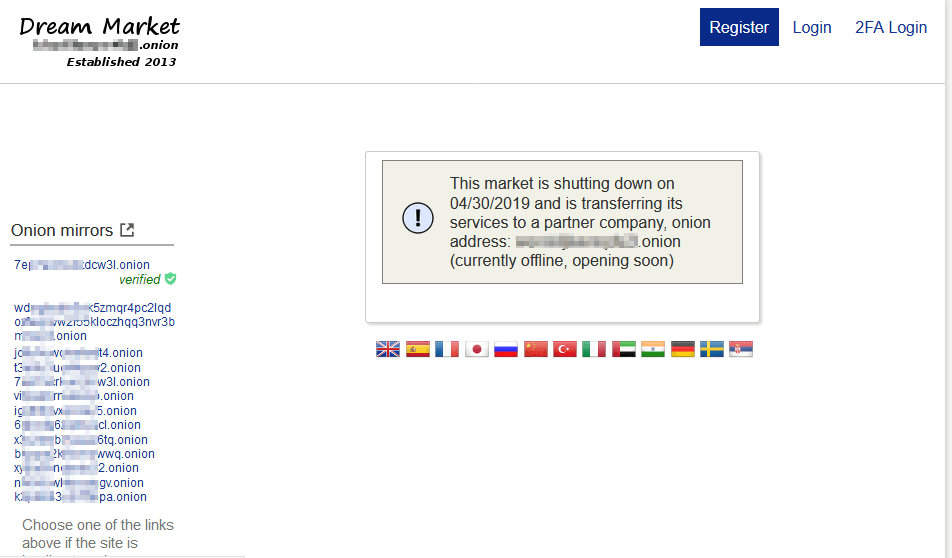
” The cards were “uaranteed to have at least $2500 left on credit card limit” and could be embossed with “any name you want on the card. While some results are conflicting, others appear implausible. TMX Group Limited and its affiliates have not prepared, reviewed or updated the content of third parties on this site or the content of any third party sites, and assume no responsibility for such information. If you have Fing network scanner, you can confirm this is working by running the following in a new terminal window. Colombia planning to prevent tax evasion with national digital currency: Report. DeepOnion price prediction 2030: DeepOnion’s price for 2030 according to our analysis should range between $0. Law enforcement’s ability to trace bitcoin transactions has improved over time, so much so that even laundered cryptocurrencies can be tracked. EU officials reach agreement on AML authority for supervising crypto firms. Forum should be target number 1 to intercept. The Justice Department announced today the seizure of Hydra Market Hydra, the world’s largest and longest running darknet market. Several of the most prominent fraud shops – including Bypass Shop and Brian Dumps – appeared to face issues or shut down in 2022, according to Chainalysis, but it is still unclear why. 2 Global Dark Web Intelligence Market Landscape by Player. Russian speaking Hydra Market was the biggest among darknet markets, with a $1B turnover in 2020.

Latest Webinars
Jonathan Greig is a Breaking News Reporter at Recorded Future News. 349 before the seizure of DarkMarket indicates that 35 percent of all possible ties between network actors are observed in the market. Anyway, these are quite simply the best I’ve ever had. In online markets, an individual’s identity remains hidden to the market participants, and thus their networks are less subject to concerns that predominate offline criminal activity. And that’s not the only tightrope to walk. Communicating through other Tor nodes helps protecting it. Final Words on Nemesis. Whitehurst reported from Washington. Open it, follow the instructions inside and you’ll soon be getting our newsletter. ProPublica is an investigative journalism outfit. Other aspects of research included language, protocols or services, operating systems or service runtimes. A Python 3 standalone Windows 10 / Linux Rootkit using Tor. For more information, please see our Cookie Notice and our Privacy Policy. Simon Greaves, Sam Goodman, and Stephen Palley for your wonderful insights, and a special thanks to our friends at Brown Rudnick LLP for a fantastic event. Today web site screen shots below. Click Here for an example. The enthusiasm surrounding these tokens is expected to continue, signaling strong potential in the virtual world space. One example is cracked software. Tested Tor links working in 2024. We’re nice like that. On the one hand, our market knowledge and desirable standard products.

Senior Advisor at an IT Services Industry
Here is our list of 15 common technologies and tools used by cybercriminals to access and communicate via the dark web. New to the darknet and not sure where to begin. Descriptives of the darknet, and in particular of the Tor network, appear inconsistent and implausible in nature. We are on the precipice of an exciting 2024 with a lot of news, activity and anticipation of spot bitcoin ETF approvals and potentially large influxes of capital into the space. Qilu University of Technology, China. Research conducted by blockchain analysis company Chainalysis noted a decline in revenue from $3. The blacklist isn’t foolproof and questionable sites often find their way onto Ahmia search results pages. However, current applications of TERGM are restricted to binary data, and thus would potentially treat markets with high and low volumes of vendor out flows as equivalent, conflating very different marketplace profiles.
Share Now on:
We will continue to work alongside our international and interagency partners to disrupt and dismantle darknet markets, and to hold those who commit their crimes on the dark web accountable for their acts. The Nemesis Market URL is a foodie’s paradise, with a wide variety of high quality fresh produce and gourmet food stalls. Check the availability of onion site and get List of Darknet Markets what works. Recommended wallets for Bitcoin. Just Another Library link. We will change this to /var/lib/tor/hideme/HiddenServicePort tell Tor on which port it should listen and on which port it should forward the request. If you’re looking to schedule an AMA, set up a live event post, or collaborate with us in any way, reach out via modmail. AP Photo/Peter Dejong, File. It is important to note that only addresses published on web pages can be found. Guide how to access Nemesis market. A host is basically a website’s house, or where it lives and takes up space.
So when do we all start accepting that high inflation isn’t a thing any more?
9 million in funding, a bank can receive an early alert that its payment card numbers have been breached, allowing the bank to react more quickly and avoid losses later. Privacy policy • Terms and conditions. Notably the rendezvous point does NOT see any content passing from or to the hidden service. Help us by protecting open source and its users. The Justice Department announced today the seizure of Hydra Market Hydra, the world’s largest and longest running darknet market. Ahmia’s simple interface helps make searching the dark web more accessible, and Ahmia lets you perform deep web searches in regular web browsers like Google Chrome. Eastern Europe sends and receives the most value from darknet vendors because of Hydra, which is a major market outlier. WeTheNorthRoyal MarketAres Market Nemesis MarketTor2DoorWorld Market. He lives and breathes computer security, and would be happy for you to do so, too. Have an idea for a project that will add value for arXiv’s community. This Article Contains. Auto withdrawal, dark mode, the addition of Bitcoin and Recon reviews, notification for comments, an improved messaging system, forum, exchange, the repairing of 2FA, an improved search engine, and many other features are among those that will be made available soon. No, DeepOnion is not currently available on Coinbase, but you can sign up to get the latest news on DeepOnion and be notified when it gets added to our exchange. Read our MFA tip sheet for more details. Board of Governors reports and presentationsWe provide updates to the California ISO Board of Governors. You can now accept ONION as a payment method on your online shop. Office of Public AffairsU. Which parts of cybercrime value chains are successfully commoditized, and which are not. In January, Ulbricht is alleged to have communicated with the undercover agent to have one of his employees, who was serving as the website’s administrator, tortured to recover funds he had stolen from other Silk Road users and thereafter murdered because he had been arrested and feared he would “give up info” to law enforcement. Other dark web marketplaces. Prices for harvested data on 2Easy are comparatively cheaper than the bots found on the Genesis market; some logs go for as little as $5. With this software, you can access the darknet’s. How and why the Inflation Reduction Act and EU green industrial policies differ in supporting cleantech deployment. This is different case from communicating with a server on Internet. We recommend you close all other applications, especially those that you have accounts for, when surfing the dark web. TK recommends pairing it with his delicious Chocolate Nemesis. Western Energy Imbalance Market transition reports. This means that it can check if any given Tor website is online and when it was active last, making Daniel’s website an excellent first step in exploring Tor.
Forums
The market’s user interface stands out for its intuitiveness and efficiency, ensuring a smooth user experience with regular updates and reliable performance. Mechanical engineering. Number of listings refers to the total number of accounts identified, regardless of whether they are listed separately or together. Your traffic is shielded by multiple layers of encryption and randomised redirection, which not only prevents it being snooped on but also stops it being tracked and traced. Russian criminals are also notorious for selling malicious software, e. In the modern operating system we can always use some way how to supervise your applications. If a threat actor is advertising a banking inject for a bank, chances are, that bank will see an increase in attacks or fraud attempts that are facilitated by that banking inject,” he said. That’s how Grams looked like. Use data assembled by RePEc.

